Zero Trust Security Architecture
In an era where cyber threats are becoming increasingly sophisticated and pervasive, traditional security models are no longer sufficient to protect sensitive data and critical systems. Enter Zero Trust Security Architecture—a paradigm shift in cybersecurity that operates on the principle of “never trust, always verify.” In this blog, we’ll explore what Zero Trust is, why it matters, and how organizations can implement it to safeguard their digital assets.
What is Zero Trust Security Architecture?
Zero Trust is a security framework that assumes no user, device, or application should be trusted by default, even if they are inside the corporate network. Instead, it requires continuous verification of identity and strict access controls at every stage of digital interaction.
The core principles of Zero Trust include:
- Verify Explicitly: Authenticate and authorize every access request based on user identity, device health, and other contextual factors.
- Least Privilege Access: Grant users and devices the minimum level of access required to perform their tasks.
- Assume Breach: Operate under the assumption that threats can come from both inside and outside the network.
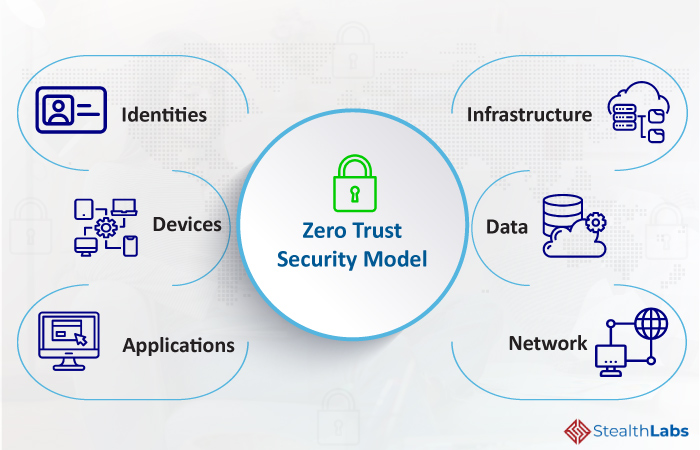
Image source: https://www.stealthlabs.com/
Why Zero Trust Matters in Today’s Threat Landscape
The traditional “castle-and-moat” security model, which focuses on defending the perimeter, is no longer effective in a world where:
- Employees work remotely and access corporate resources from various locations and devices.
- Cloud adoption and hybrid work environments have blurred the boundaries of the corporate network.
- Cybercriminals are using advanced tactics like phishing, ransomware, and insider threats to breach systems.
Zero Trust addresses these challenges by:
- Eliminating Implicit Trust: By verifying every access request, Zero Trust minimizes the risk of unauthorized access.
- Reducing Attack Surface: Least privilege access ensures that even if a breach occurs, the damage is contained.
- Enhancing Visibility: Continuous monitoring provides real-time insights into user activity and potential threats.
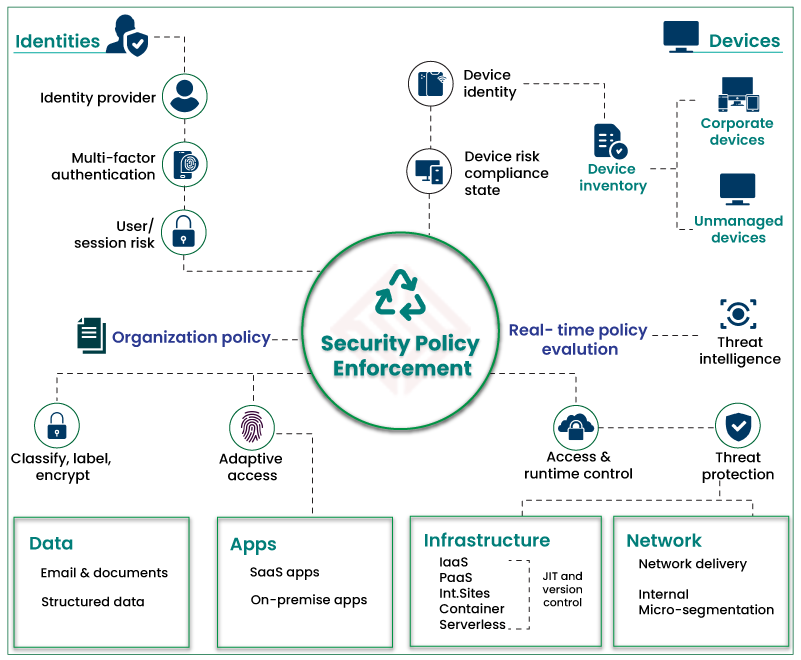
Key Components of a Zero Trust Architecture
Implementing Zero Trust requires a holistic approach that integrates multiple technologies and practices. Here are the key components:
- Identity and Access Management (IAM):
- Use multi-factor authentication (MFA) and single sign-on (SSO) to verify user identities.
- Implement role-based access control (RBAC) to enforce least privilege policies.
- Micro-Segmentation:
- Divide the network into smaller, isolated segments to limit lateral movement in case of a breach.
- Endpoint Security:
- Ensure all devices accessing the network are secure, up-to-date, and compliant with security policies.
- Continuous Monitoring and Analytics:
- Leverage AI and machine learning to detect anomalies and respond to threats in real time.
- Encryption:
- Encrypt data in transit and at rest to protect it from unauthorized access.
- Policy Enforcement:
- Use tools like Secure Access Service Edge (SASE) to enforce security policies across all users, devices, and applications.
Benefits of Zero Trust Security
Adopting a Zero Trust framework offers several advantages:
- Improved Security Posture: By eliminating implicit trust, Zero Trust significantly reduces the risk of data breaches and cyberattacks.
- Regulatory Compliance: Zero Trust helps organizations meet stringent data protection regulations like GDPR, CCPA, and HIPAA.
- Enhanced Visibility: Continuous monitoring provides a clear view of user activity and potential vulnerabilities.
- Scalability: Zero Trust is adaptable to hybrid and multi-cloud environments, making it ideal for modern IT infrastructures.
Challenges in Implementing Zero Trust
While Zero Trust offers significant benefits, its implementation can be complex and resource-intensive. Common challenges include:
- Cultural Shift: Moving from a perimeter-based model to Zero Trust requires a change in mindset across the organization.
- Integration with Legacy Systems: Older systems may not support Zero Trust principles, requiring upgrades or replacements.
- Cost and Complexity: Implementing Zero Trust involves investing in new technologies and skilled personnel.
How to Get Started with Zero Trust
Transitioning to a Zero Trust architecture is a journey, not a one-time project. Here’s a step-by-step approach to get started:
- Assess Your Current Environment:
- Identify critical assets, users, and devices.
- Evaluate existing security controls and gaps.
- Define Your Zero Trust Strategy:
- Establish clear goals and priorities.
- Develop a roadmap for implementation.
- Implement Key Technologies:
- Deploy IAM, MFA, and endpoint security solutions.
- Use micro-segmentation and encryption to protect data.
- Monitor and Optimize:
- Continuously monitor user activity and system performance.
- Refine policies and controls based on insights and feedback.
- Educate and Train Employees:
- Foster a culture of security awareness.
- Provide training on Zero Trust principles and best practices.
Conclusion
In a world where cyber threats are constantly evolving, Zero Trust Security Architecture offers a proactive and resilient approach to protecting sensitive data and critical systems. By eliminating implicit trust and enforcing strict access controls, organizations can significantly reduce their risk of breaches and ensure compliance with regulatory requirements.
At ConnexDotz, we specialize in helping businesses design and implement Zero Trust frameworks tailored to their unique needs. Whether you’re just starting your Zero Trust journey or looking to enhance your existing security posture, our team is here to guide you every step of the way.
Ready to embrace the future of cybersecurity? Contact us today to learn more about our Zero Trust solutions and how we can help your organization stay secure in a perimeter less world.
